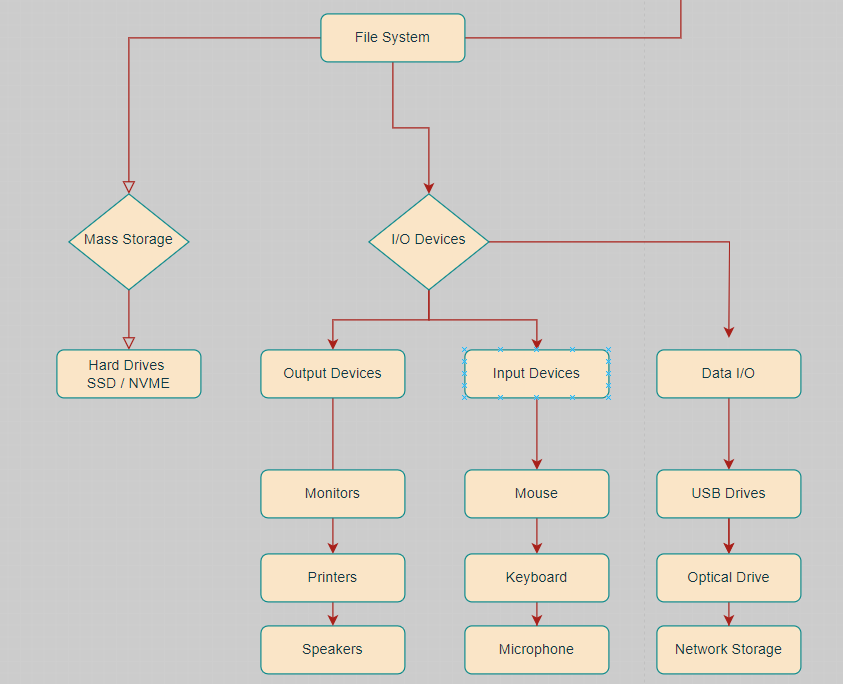
Summary Blog Post Understanding the fundamental concepts underlying operating systems provides a solid foundation for comprehending the features, structures, and mechanisms employed by contemporary operating systems. This knowledge is valuable for a range of roles involving system administration, software development, and working with computer systems in various domains. While being in this course, I have gained new insights into how operating systems theory works as well as understanding the fundamental concepts that underlie operating systems. When these concepts combine, they form the foundation for the design and functionality of contemporary operating systems. Below are my responses for the final questions for this course. I will say that this course was a vast venture into how the theory and design of operating systems truly work and function. Describe Features of Contemporary Operating Systems and Their Structures St...

